Data Protection Impact Assessment (DPIA) of processing
We specialise in assessing the impact of processing on the protection of personal data.
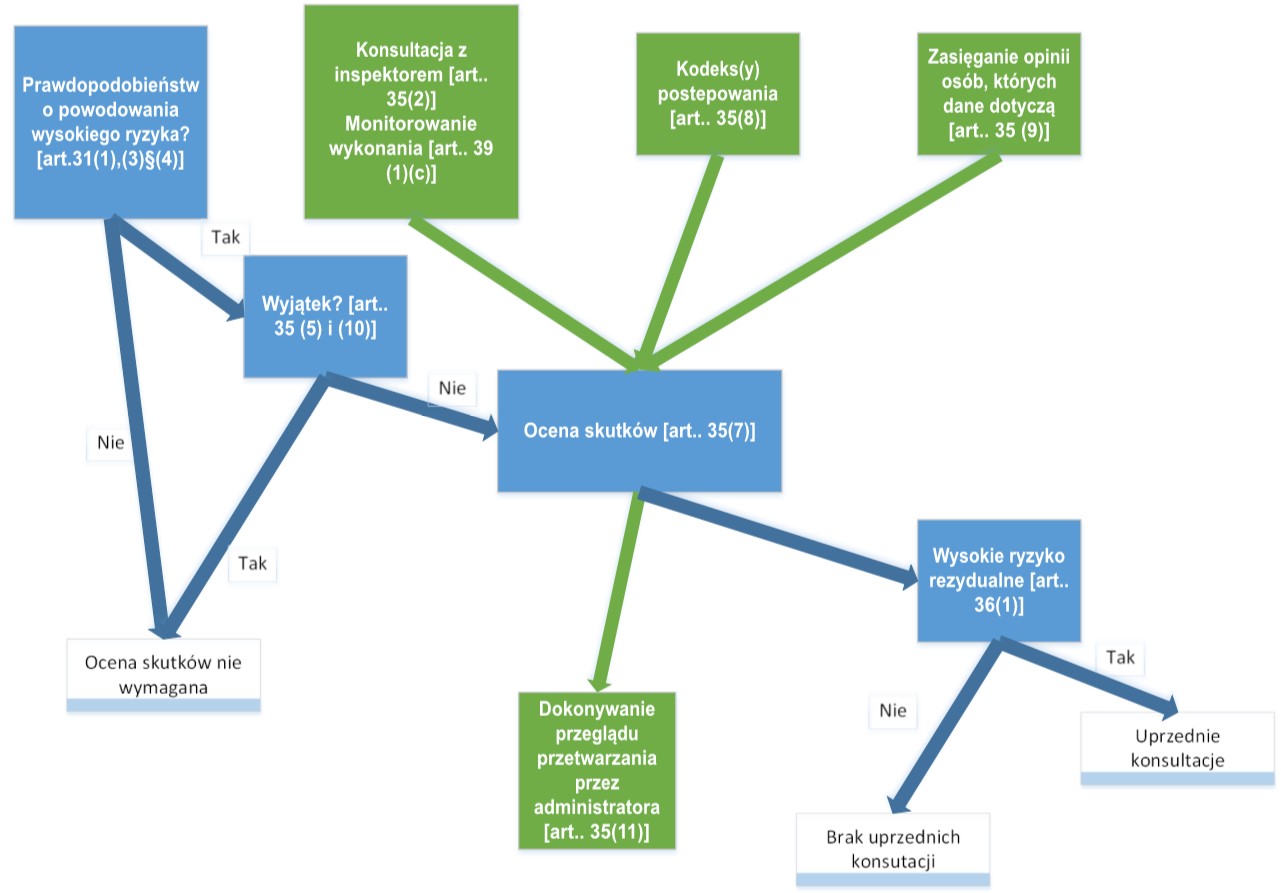
We are one of the few companies that advise the largest entities in Poland in this area. A data protection impact assessment is carried out when it is highly likely that the type of processing could result in a high risk to the rights and freedoms of data subjects.
On 8 July 2019, the announcement of the President of the Office for the Protection of Personal Data of 17 June 2019 was published, containing a list of types of personal data processing operations that require an assessment of the impact of the processing on the protection of personal data. Such operations are, for example, a system for monitoring employees’ working hours and the flow of information in the tools they use (email, internet).
Personal Data Administrators, and as a result Data Protection Officers and IT System Administrators of systems used for the processing of personal data, are obliged to assess the effects of processing on the protection of personal data.
The same pattern of conduct as for the general risk assessment can be used for the data protection impact assessment, highlighting in the different stages (from context description to risk handling) those elements that have a material impact on the impact that a data breach may have on data subjects.
The purpose of the impact assessment is to estimate the risk, which we understand as hypothetical scenarios of high-risk events described by
- The type of personal data, e.g. customers’ personal data.
- Sources of risk.
- Vulnerabilities that can be exploited in resources supporting the processing of personal data.
- An event we fear will occur, such as a personal data leak.
- Impact on data subjects, e.g. discrimination, financial loss, social media defamation.
We use proven practices and methodologies we have developed.
The impact assessment process is most often carried out in the following steps:
Context
Defining and describing the environment for the processing of personal data. Indication of the purposes of the processing.
- Purposes of processing, description of the processing environment.
- Description of data processing.
- Purpose, information, type of rights to be secured.
- Description of personal data.
- List of supporting assets.
Security
Identify current and planned measures to ensure compliance and control privacy risks.
- A list of security measures for personal data in organizational, IT and physical aspects.
Risk
Privacy risk assessment to ensure adequacy and appropriate risk planning.
- Identify sources of risk. We answer the questions: who and why?
- Vulnerability indication.
- Description of risk events. We answer the questions: what and how? For unauthorized access to data, unwanted modification and disappearance of data.
- Threats indication.
- We determine the probability levels.
- We describe and estimate the effects on individuals.
Decision
Decide how to comply with privacy and risk rules.
- Risk evaluation.
- Indication of countermeasures: safeguards.
- Developing risk management plans.
- DPO’s opinion.
- Opinion of data subjects.
- Formal validation.
- If the risk is still not acceptable, consult the supervisory authority.